CDPSvc DLL Hijacking - From LOCAL SERVICE to SYSTEM
A DLL hijacking “vulnerability” in the CDPSvc service was reported to Microsoft at least two times this year. As per their policy though, DLL planting issues that fall into the category of PATH directories DLL planting are treated as won’t fix , which means that it won’t be addressed (at least in the near future). This case is very similar to the IKEEXT one in Windows Vista/7/8. The big difference is that CDPSvc runs as LOCAL SERVICE instead of SYSTEM so getting higher privileges requires an extra step.
CDPSvc DLL Hijacking
Before we begin, I’ll assume you know what DLL hijacking is. It’s probably one of the oldest and most basic privilege escalation techniques in Windows. Besides, the case of the CDPSvc service was already well explained by Nafiez in this article: (MSRC Case 54347) Microsoft Windows Service Host (svchost) - Elevation of Privilege.
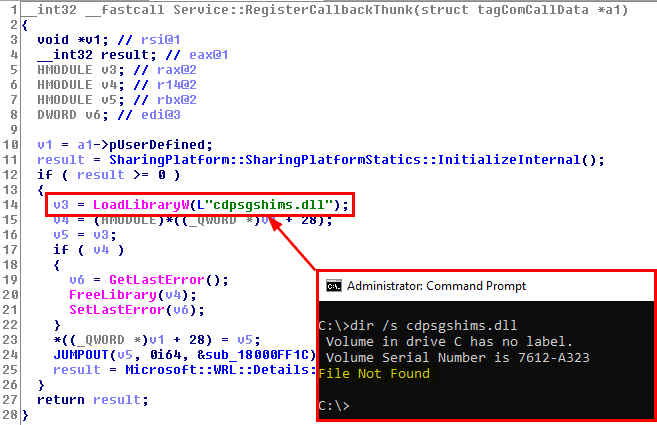
Long story short, the Connected Devices Platform Service (or CDPSvc) is a service which runs as NT AUTHORITY\LOCAL SERVICE and tries to load the missing cdpsgshims.dll DLL on startup with a call to LoadLibrary(), without specifying its absolute path.
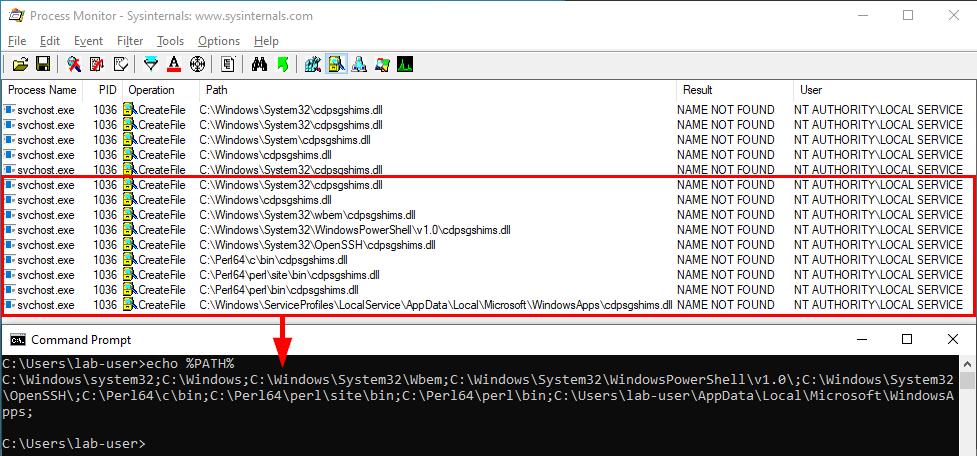
Therfore, following the DLL search order of Windows, it will first try to load it from the “system” folders and then go through the list of directories which are stored in the PATH environment variable. So, if one of these folders is configured with weak permissions, you could plant a “malicious” version of the DLL and thus execute arbitrary code in the context of NT AUTHORITY\LOCAL SERVICE upon reboot.
Note: the last PATH entry varies depending on the current user profile. This means that you will always see this folder as writable if you look at your own PATH variable in Windows 10. If you want to see the PATH variable of the System, you can check the registry with the following command: reg query "HKLM\SYSTEM\CurrentControlSet\Control\Session Manager\Environment" /V Path.
That’s it for the boring stuff. ![]() Now let’s talk about some Windows internals and lesser known exploitation techniques.
Now let’s talk about some Windows internals and lesser known exploitation techniques. ![]()
A Word (Or Maybe Two…) About Tokens And Impersonation
In my previous article, I discussed the specific case of service accounts running without impersonation privileges. As it turns out, it’s not the case of CDPSvc so we will be able to take advantage of this. However, I realize that I didn’t say much about the implications of each impersonation privilege. It’s not overly complicated but I know that it’s easy to overlook this kind of things because there are so many other things to learn.
Since I worked quite a bit on the inner working of tools such as RottenPotato or JuicyPotato, I’d like to share what I learned in an hopefully clear and concise way. If you’re already familiar with these concepts, you may skip to the next part.
Token Types
First things first. Let’s talk about tokens. There are 2 types of tokens: Primary tokens and Impersonation tokens. A Primary token represents the security information of a process whereas an Impersonation token represents the security context of another user in a thread.
- Primary token: one per process.
- Impersonation token: one per thread which impersonates another user.
Note: an Impersonation token can be converted to a Primary token with a call to DuplicateTokenEx().
Impersonation Levels
An Impersonation token comes with an impersonation level: Anonymous, Identification, Impersonation or Delegation. You can use a token for impersonation only if it has an Impersonation or Delegation level associated with it.
- Anonymous: The server cannot impersonate or identify the client.
- Identification: The server can get the identity and privileges of the client, but cannot impersonate the client.
- Impersonation: The server can impersonate the client’s security context on the local system.
- Delegation: The server can impersonate the client’s security context on remote systems.
Impersonation
Regarding the impersonation methods, there are 3 different ways to create a process as a different user in Windows as I far as I know.
- CreateProcessWithLogon() - (documentation)
This function doesn’t require any specific privilege. Any user can call this function. However you must know the password of the target account. That’s typically the method used by runas.
- CreateProcessWithToken() - (documentation)
This function requires the SeImpersonatePrivilege privilege, which is enabled by default (for the LOCAL SERVICE account). As an input, it requires a Primary token.
- CreateProcessAsUser() - (documentation)
This function requires the SeAssignPrimaryTokenPrivilege and SeIncreaseQuotaPrivilege privileges, which are both disabled by default (for the LOCAL SERVICE account) but only SeAssignPrimaryTokenPrivilege really needs to be enabled. SeIncreaseQuotaPrivilege will be transperently enabled/disabled during the API call. As an input, it also requires a Primary token.
| API function | Privilege(s) required | Input |
|---|---|---|
CreateProcessWithLogon() |
None | Domain / Username / Password |
CreateProcessWithToken() |
SeImpersonatePrivilege |
Primary token |
CreateProcessAsUser() |
SeAssignPrimaryTokenPrivilege AND SeIncreaseQuotaPrivilege
|
Primary token |
The CDPSvc Case
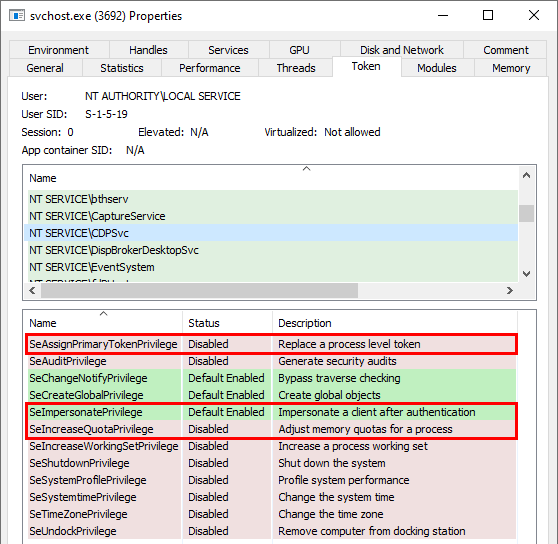
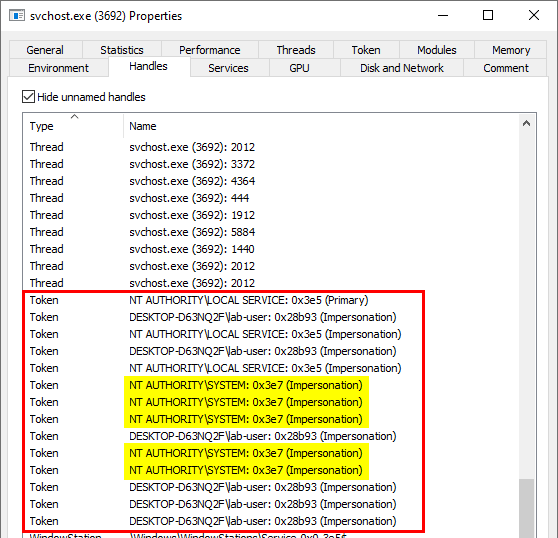
As you can see on the below screenshot, the process in which CDPSvc runs has the three privileges I’ve just talked about so it can impersonate any local user with CreateProcessWithToken() or CreateProcessAsUser() provided that you have a valid token for this user.
As a conclusion, we have the appropriate privileges to impersonate NT AUTHORITY\SYSTEM. The second thing we need is a valid token but how can we get one of them? ![]()
Bringing Back An Old Technique From The Dead: Token Kidnapping
In the old days of Windows, all services ran as SYSTEM, which means that when one of them was compromised all the other services and the host itself were also compromised. Therefore Microsoft added some segregation and introduced two other accounts with less privileges: NETWORK SERVICE and LOCAL SERVICE.
Unfortunately, this wasn’t enough. Indeed, if a service running as LOCAL SERVICE was compromised for example, it could execute code in any other service running as the same user account, access its memory space and extract privileged impersonation tokens: this is the technique called Token Kidnapping, which was presented by Cesar Cerrudo at several conferences in 2008.
To counter this attack, Microsoft had to redesign the security model of the services. The main feature they implemented was Service Isolation. The idea is that each service runs with a dedicated Security Identifier (SID). If you consider a service A with SID_A and a service B with SID_B, service A won’t be able to access the ressources of service B anymore because the two processes are now running with two different identities (although it’s the same account).
Here is a quote from MS Blog, Token Kidnapping in Windows.
The first issue to address is to make sure that two services running with the same identity not be able to access each other’s tokens freely. This concern has been mostly addressed with service hardening done in Windows Vista and above. There are some minor changes that would need to be done to strengthen service hardening to close some gaps identified during our investigation of this issue.
OK so, basically, you’re telling me that Token Kidnapping is now useless because of Service Isolation. What’s the point in talking about that then? ![]()
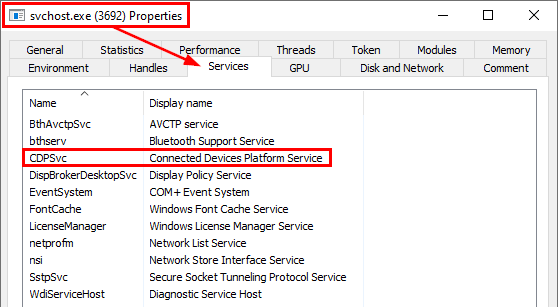
Well, the fun fact about CDPSvc is that it runs within a shared process so Service Isolation is almost pointless here since it can access the data of almost a dozen services. CDPSvc runs within a shared process by default only if the machine has less than 3.5GB of RAM (See Changes to Service Host grouping in Windows 10). The question is, among all these services, is there at least one that leaks interesting token handles?
Let’s take a look at the properties of the process once again. Process Hacker provides a really nice feature. it can list all the Handles that are open in a given process.
It looks like the process currently has 5 open Handles to Impersonation tokens which belong to the SYSTEM account. How convenient! ![]()
Fine! How do we proceed?! ![]()
A Handle is a reference to an object (such as a Process, a Thread, a File or a Token for example) but it doesn’t hold the address of the object directly. It’s just an entry in an internally maintained table where the “actual” address is stored. So, it can be seen as an ID, which can be easily bruteforced. That’s the idea behind the Token Kidnapping technique.
Token Kidnapping consists in opening another process and then bruteforcing the open Handles by duplicating them inside the current process. For each valid Handle, we check whether it’s a Handle to a Token, if it’s not the case, we go to the next one.
If we find a valid Token Handle, we must check the following:
- The corresponding account is
SYSTEM? - Is it an Impersonation token?
- The Impersonation Level of the token is at least Impersonation?
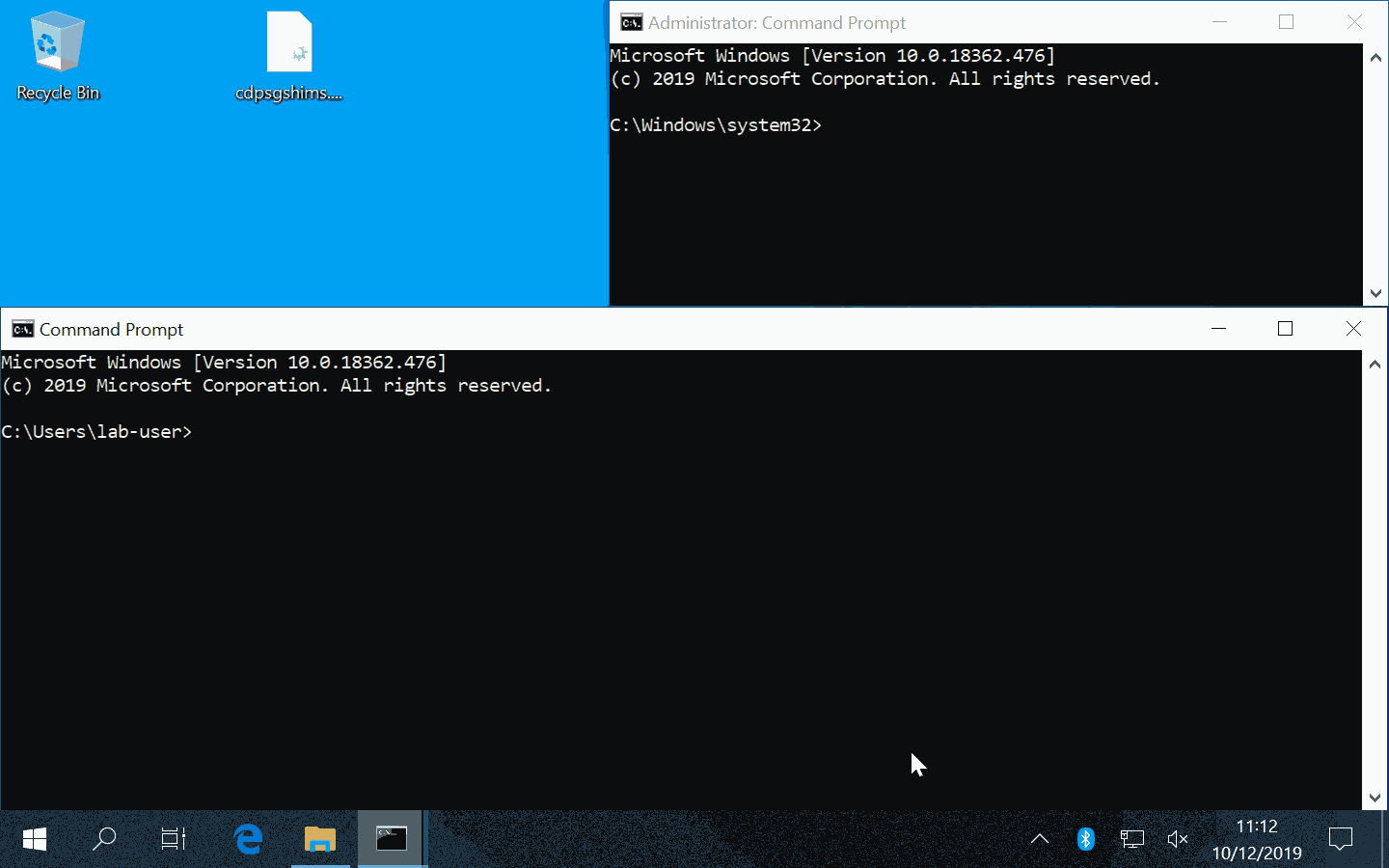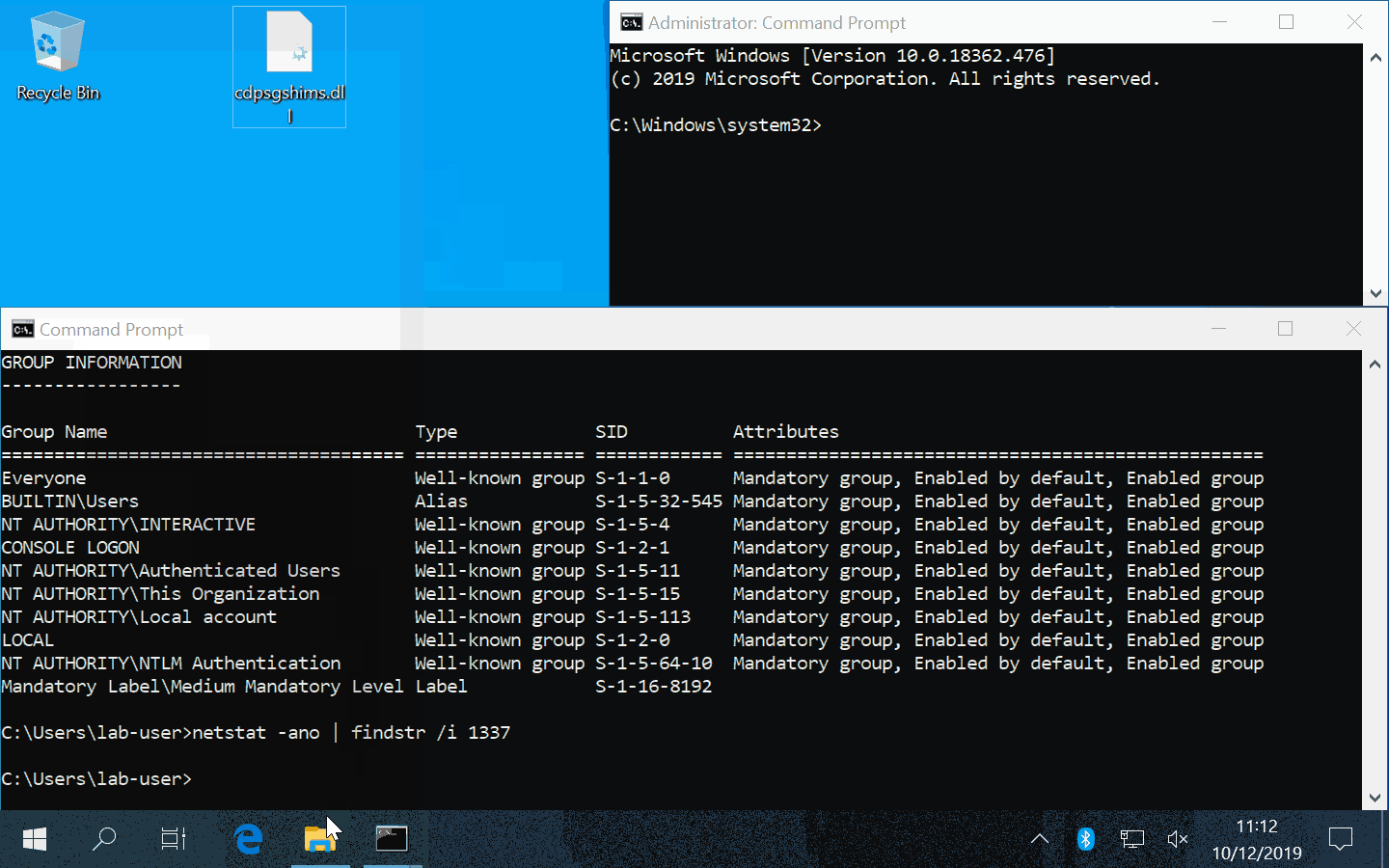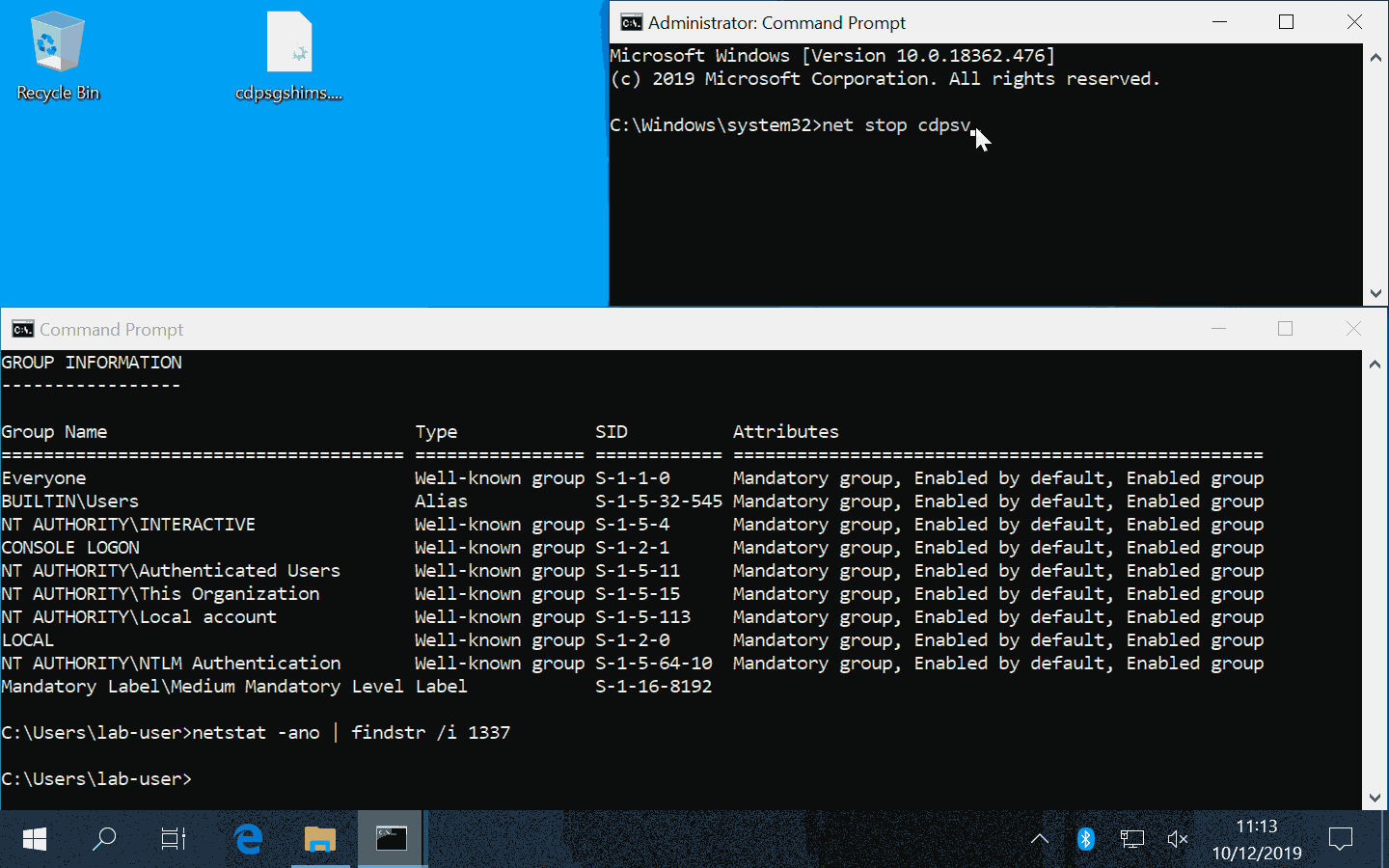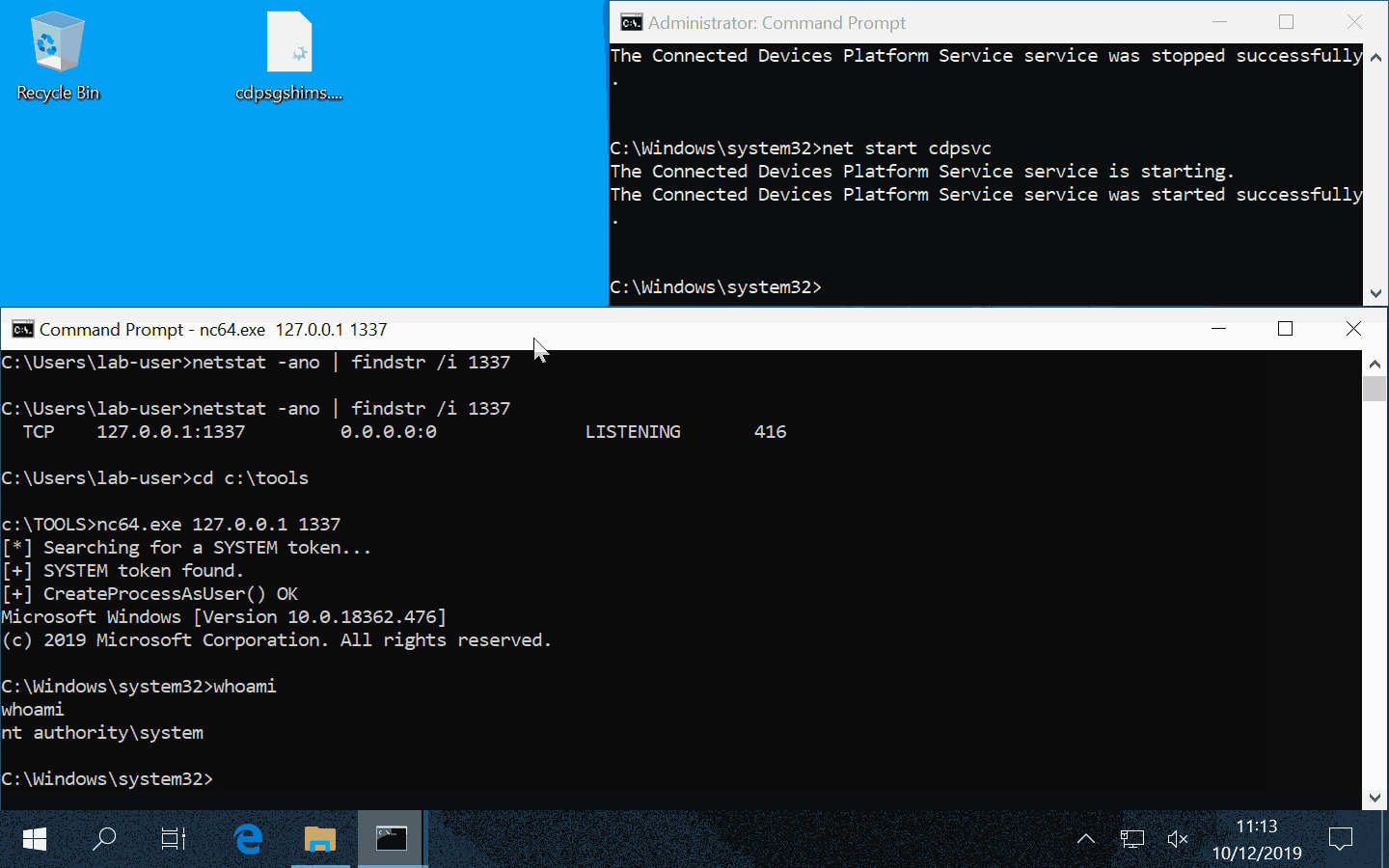
Of course, because of Service Isolation, this technique can’t be applied to services running in different processes. However, if you are able to “inject” a DLL into one of these services, you can then access the memory space of the corresponding process without any restrictions. So, you can apply the same bruteforce technique from within the current process. And, once you’ve found a proper impersonation token, you can duplicate it and use the Windows API to create a process as NT AUTHORITY\SYSTEM. That’s as simple as that.
No conclusion for this post. I just hope that you learned a few things. Here is the link to my PoC.
Demo
Links & Resources
(MSRC Case 54347) Microsoft Windows Service Host (svchost) - Elevation of Privilege
https://nafiez.github.io/security/eop/2019/11/05/windows-service-host-process-eop.htmlWindows 10 Persistence via PATH directories - CDPSvc
https://www.a12d404.net/windows/2019/01/13/persistance-via-path-directories.htmlCesar Cerrudo - Token Kidnapping
https://dl.packetstormsecurity.net/papers/presentations/TokenKidnapping.pdfMS Blog - Token Kidnapping in Windows
https://blogs.iis.net/nazim/token-kidnapping-in-windowsMSRC - Triaging a DLL planting vulnerability
https://msrc-blog.microsoft.com/2018/04/04/triaging-a-dll-planting-vulnerability/MSDN - Access Tokens
https://docs.microsoft.com/en-us/windows/win32/secauthz/access-tokensMSDN - Impersonation Levels
https://docs.microsoft.com/en-us/windows/win32/secauthz/impersonation-levels